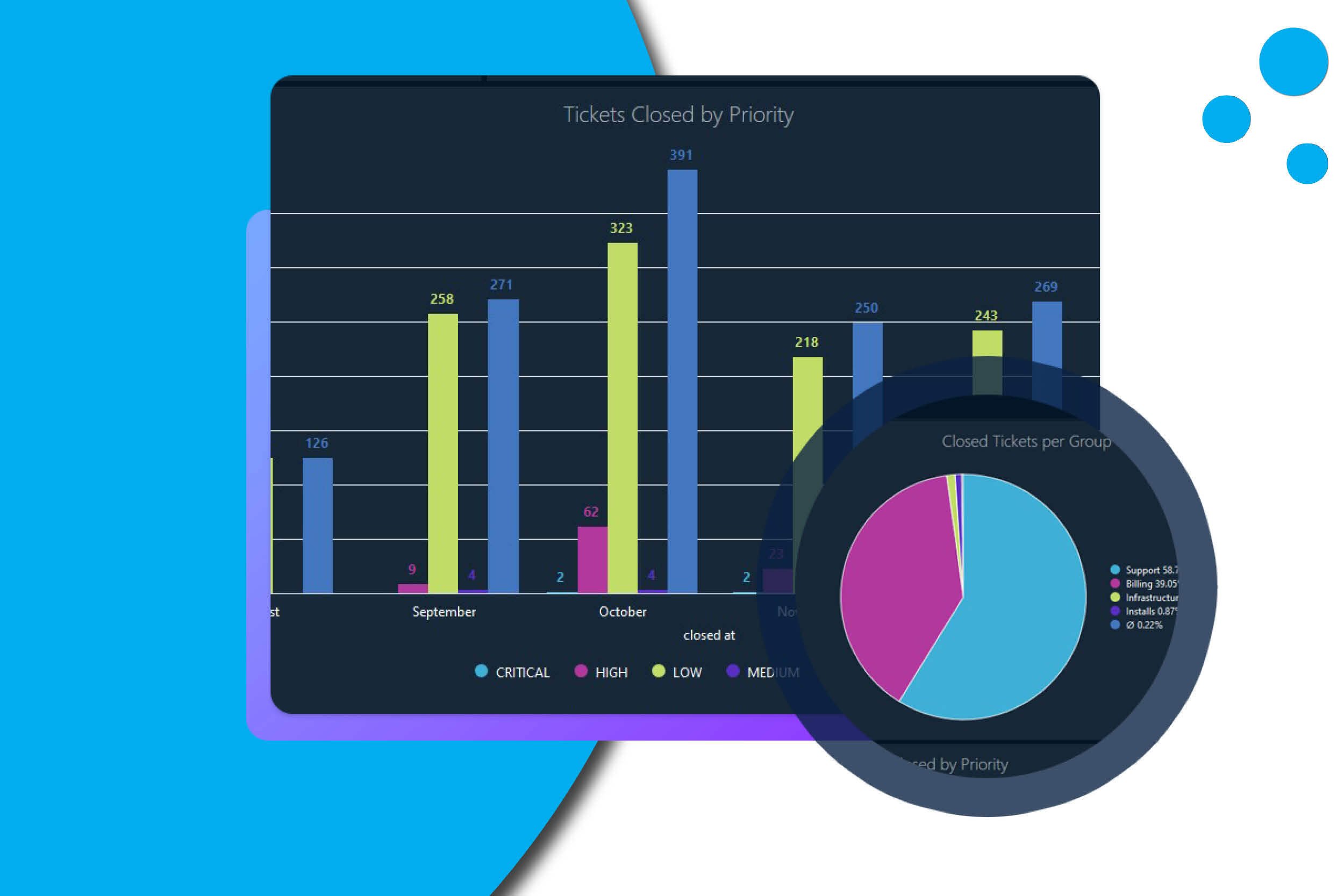
Tips to Optimize your Ticket Resolution Process
Customer support is critical to the sustained growth of an Internet Service Provider as it directly impacts customer satisfaction and loyalty....
2 min read
 Dawn Rorick
:
Jul 3, 2024
Dawn Rorick
:
Jul 3, 2024

As an Internet Service Provider (ISP), you are entrusted with a treasure trove of sensitive customer information. From personal details and browsing history, to financial data and online activities, the data you collect and store is a prime target for cybercriminals. Protecting this data is not just a legal obligation; it’s a moral imperative and a cornerstone of building and maintaining customer trust. Let’s explore the essential data protection and privacy measures that every ISP should implement.
Data encryption is the digital equivalent of a fortress wall, protecting your data from prying eyes. It involves converting data into an unreadable format that can only be deciphered with the correct decryption key. By encrypting data both in transit (as it travels over your network) and at rest (when it’s stored on your servers), you significantly reduce the risk of unauthorized access and data breaches.
Not everyone in your organization needs access to all customer data. Implementing strict access controls ensures that only authorized personnel can view or modify sensitive information. Role Based Access Control (RBAC) assigns permissions based on job roles, ensuring that employees can only access the data necessary for their specific tasks. This prevents accidental or intentional data misuse and reduces the risk of insider threats.
Just like regular health checkups can detect potential health problems early on, vulnerability assessments can identify weaknesses in your systems and software before attackers exploit them. These assessments involve scanning your network and applications for known vulnerabilities, misconfigurations, and potential entry points for hackers. By proactively addressing these vulnerabilities, you can strengthen your defenses and reduce the risk of a successful attack.
Your customer data deserves a secure vault, not a leaky bucket. Implementing secure data storage practices means encrypting data at rest, using strong access controls for storage systems, and regularly backing up data to ensure its availability in case of a disaster or cyberattack. It also means having a data retention policy in place to ensure that you’re not holding onto data longer than necessary, which can reduce your risk profile.
The less data you collect and store, the less you have to lose in a breach. Data minimization is the practice of collecting only the data that’s absolutely necessary for your business operations. By minimizing the amount of sensitive information you hold, you reduce your attack surface and the potential impact of a data breach. It’s about striking a balance between the data you need to provide services and the data you don’t need to put at risk.
In our next blog post, we’ll delve into the importance of employee awareness and training, empowering your staff to become a frontline defense against cyber threats. Stay tuned!

Customer support is critical to the sustained growth of an Internet Service Provider as it directly impacts customer satisfaction and loyalty....

1 min read
One of the most popular puzzles of the ’70s was the Rubik’s Cube. In 1974 the Rubik’s Cube was invented by Ernő Rubik and would go on to live...

Artificial intelligence is becoming part of daily life for broadband providers. It supports ticket triage, summarizes documentation, and helps teams...